Medium Access Protocols
The Data Link Layer is responsible for the transmission of data between two nodes. So, the Data Link Layer uses some protocols to access the medium.
As we know, the Data Link layer has to sub-layers
1. Logical Link Control (LLC): The main responsibility of Logical link control is flow control.
Keep in mind: If there is a dedicated link between the sender and the receiver (i.e., Mesh Topology), then there is no need for MAC. Only the logical link control layer is sufficient.
2. Multiple Access Control (MAC): The main responsibilities of Medium Access control (MAC) are
- Framing
- Physical Addressing
- Error Control
- Access Control
Keep in mind: if there is no dedicated link present (i.e., BUS Topology), then multiple stations can access the same medium simultaneously. So, MAC protocols are required to avoid collision and crosstalk.
Real Life Example, if a classroom is full of students when a teacher asks a question and all the students start answering at the same time, then crosstalk and collisions factors come to occur. Then, it is the job of the teacher (MAC protocols) to manage all students, with one answer, one at a time.
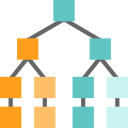
There are three major types of Medium Access Control Protocols. The following figure shows the types

A short introduction of each category is explained below
1. Random Access Protocols
In random access protocols, all stations are independent to access the medium. It just depends on the channel’s state (idle or busy). If the medium is idle, then transmission is possible; otherwise, wait for its transmission. However, if more than one station sends the data over a common medium, then collision is possible.
Further types of Random Access Protocols are
- Aloha
- CSMA
- CSMA/CD
- CSMA/CA
2. Control Access Protocols
All stations in control access protocols seek information from one another to find which station has the right to data transmission. It allows only one station (device) to send data at a time to avoid collision of frames on shared medium.
Further types of controlled-access methods are:
- Reservation
- Polling
- Token Passing
3. Channelization Protocols
In channelization protocols, the available bandwidth of the transmission medium is shared with the prospect of time, frequency, or code for multiple stations to access the channel simultaneously.
Methods for channelization are
- Frequency Division Multiple Access (FDMA)
- Time Division Multiple Access (TDMA)
- Code Division Multiple Access (CDMA)