ALOHA In Random Access Protocols
Aloha was designed for WLAN but is also applicable for shared media. In Aloha, multiple stations can transmit data at the same time, which leads to collision and loss of data.
Before starting the topic, you must know about the following points
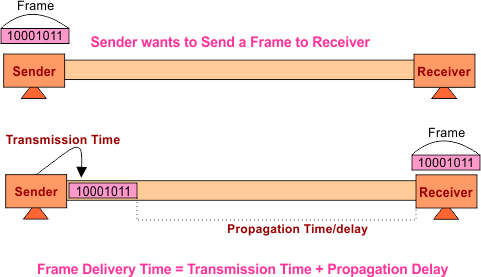
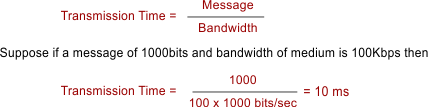
- Transmission Time: Time to put the entire message from station to medium.
- Propagation Time: Time spent by a message over medium to move toward the receiving end.
Versions of Aloha Protocol
Aloha has two version which are explained below in detail
1. Pure Aloha
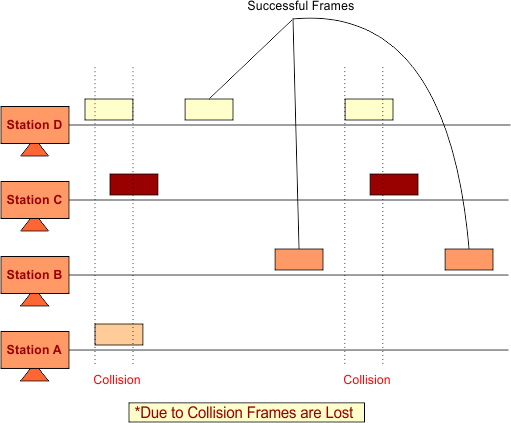
In pure ALOHA, frames are continuously transmitted over medium without any wait. Whenever a station holds an available frame, then it sends that frame. If there is a collision in frames, then the frames are lost, and the sender waits for a random amount of time before retransmission of the frame.
If, during the transmission time of one station, any other station also transmits the data on the same channel, then A collision occurs. The following diagram explains all.
Significant Features of Pure Aloha are
I. Random Access Transmission: Any device can transmit data anytime.
II. Acknowledgement: The sender waits for an acknowledgment signal for a random amount of time; if acknowledgment is not received, retransmission comes into the picture. Back-off time method is used for retransmission so that retransmission should be safe.
III. WLAN: It is used in Wireless Local Area Networks but is also applicable for shared media.
Note: As it is used in WLAN, it considers only transmission time, not propagation time
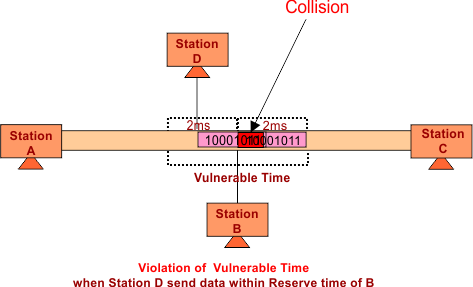
IV. Vulnerable Time: It is the time after which the other device is capable of transmitting the data on the same shared medium. It is the double transmission time.
Suppose the transmission time of Station A is 2ms. In Aloha, for successful transmission, it is necessary that no other station transmits data 2ms before when Station-A starts its transmission. So,
Vulnerable Time = 2* Transmission Time
The following figure shows the Vulnerable Time
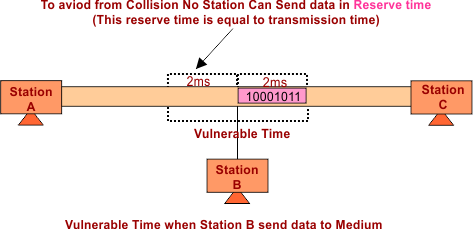
If there is a Vulnerable Time violation, a collision occurs, as shown in the following figure.
V. Throughput/Efficiency Formula: Efficiency = G * e – 2 G
G is the total number of stations that want to transfer data at transmission time. 2 is derived from vulnerable time.
Maximum throughput/ Efficiency in Aloha when G = ½. It means that half of the stations want to transmit data in transmission time. Then efficiency will be the maximum.
When G=1/2 then Efficiency = 18.4%
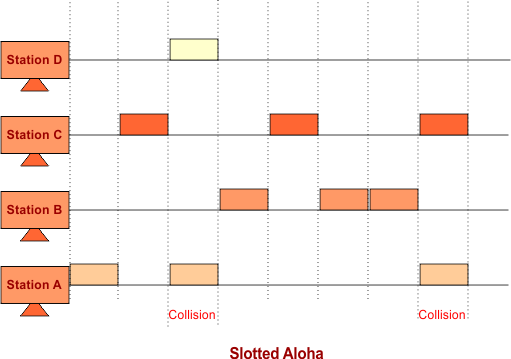
2. Slotted Aloha
Slotted Aloha is similar to pure Aloha, except for using time slots. Slotted Aloha holds time slots, the sending of data are allowed only at the beginning of time-slots. If any station misses out on the allowed time, it must wait for the next time slot. This reduces the probability of collision.
Keep in mind: Time Slot is always equal to the transmission time so that the message can be delivered.
But still, there is a chance of collision when two or more stations appear at the end of the previous slot to transfer data.
Throughput/Efficiency Formula: Efficiency = G * e – 1 G
G is the total number of stations that want to transfer data at transmission time. 1 is derived from the vulnerable time of slotted Aloha.
Maximum throughput/ Efficiency in Aloha when G = 1. It means when all of the stations want to transmit data in their transmission time slot, then efficiency will be the maximum.
When G=1 then Efficiency = 36.8%
Note: Double the efficiency as compared to pure Aloha
Comparisons of Pure Vs. Slotted Aloha
| Pure Aloha | Slotted Aloha |
| Any device can transmit data at any time: | Every device sends data at the beginning of the time slot. |
| Single efficiency (18.4%) | Double the efficiency (36.8%) |
| Vulnerable time = transmission time | Vulnerable time = 2 x transmission time |