Controlled Access Protocols
In controlled access protocols, there is no chance of collision because stations get information from one another to find which station has the right to send. Control access protocols allow only one node to send at a time. In this way, the collision of messages on shared media can be avoided.
The 3 basic controlled-access methods which are:
1. Reservation
According to the reservation, every station needs to make a reservation before transmitting the data.
- If there are N stations, then reservation slots will also be N, So each station has its own mini-reservation slot.
- If station-1 has a frame to send, it transmits bit-1 to its corresponding mini reservation slot.
- No other station is allowed to transmit data during the reservation slot of any other station.
- Transmission of frames from a station depends upon the order of reservation of slots.
- After the first reservation interval (data transmission period), the next reservation interval begins.
- In this way, there will never be any collisions.
Note: As sending one bit in a slot. So it is called a mini-reservation slot.
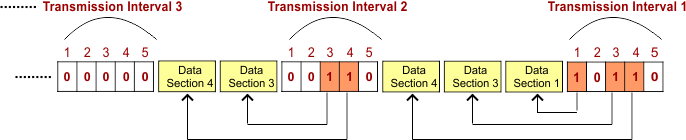
Example: The following figure shows a situation with 5 stations and 5 mini-reservation slots.
- In the first data transmission interval, only stations 1, 3, and 4 are sending data.
- In the second interval, only stations 3 and 4 have made a reservation and sent data.
- And in the last transmission interval, no station is sending data, and so on.
2. Polling
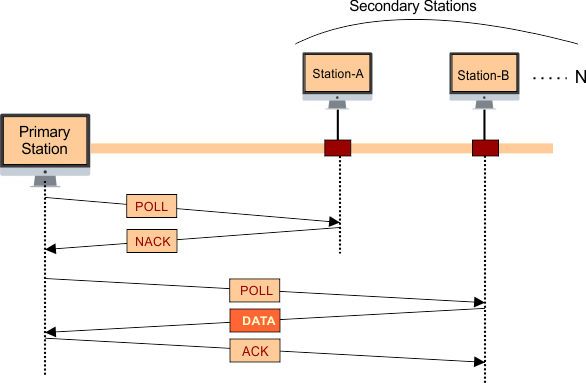
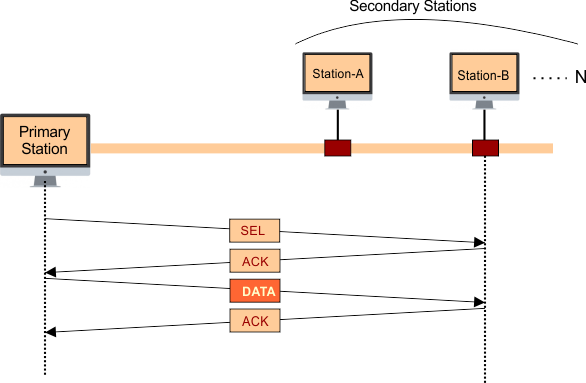
- In polling, one station acts as a primary station (controller), and the others are considered as secondary stations. All data exchanges are made through the primary station.
- The polling process is similar to the RollNo-Call performed in class by the teacher. As the teacher is a controller, all questions and answers are made through the controller.
In Polling, there are two functions used: one is POLL, and the other is SELECT. Let explain
I. POLL Function
When the primary station wants to send the data to a secondary station, then it uses the POLL function.
- If the primary station sends a POLL SIGNAL to a secondary station, and the corresponding secondary station is not ready to send data, then it sends NACK (Negative Acknowledgement) instead of data to the primary station.
- Otherwise, the secondary station sends data back to the primary station.
- In the end, if data is received at the primary station successfully, then the primary station sends ACK to the corresponding secondary station for confirmation.
II. SELECT Function
When a primary station wants to send the data to a secondary station, then it uses the Select function.
- When the primary station sends a SELECT SIGNAL to a secondary station, then the corresponding secondary station sends ACK back to the primary station.
- As the Primary station receives ACK, it sends data to the corresponding secondary station.
- In the end, if data is received at the corresponding secondary station successfully, then it sends ACK to the primary station for confirmation.
3. Token Passing
Token passing uses a special signal called a ticket or token. A token is a special bit pattern or a small message that moves from one station to the other in some predefined order (clock or anti-clockwise).
According to token passing,
- In token passing, all stations are logically connected with each other in the form of a ring. If any station wants to send data, then first, it has to get a token. Only one token is used in the entire network.
Any station in the network may transmit the data only if it has a token. Without a token/ticket, the device cannot communicate with the network. So, there is no chance of collision in controlled access protocols.
When a computer in a token ring standard network wants to send a message, it must follow the following.
- Gets the token
- Puts the data in a token
- Adds the address of the receiving computer
Token passes from computer to computer; the computer whose address matches the mentioned (destination) address in the token will receive the data.
It also sends the acknowledgment signals to the sender to indicate that the data has been received successfully. Token rings follow the ring topology. That’s why it can also be used in start topology.

Keep in Mind: the station that contains the token is called the current station, and the station that will get the token after the release of the current station is called the successor. The station from where the current station gets the token is called the predecessor.