2-Tier Architecture in DBMS
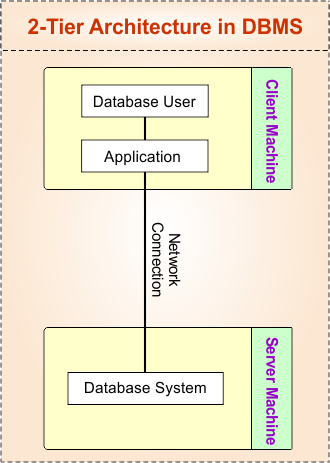
In Database Management Systems (DBMS), a 2-Tier Architecture is a client-server model where any number of client application directly communicates with the database server. The client machine provides the user interface using the application and handles the logic, while the server stores and manages the database.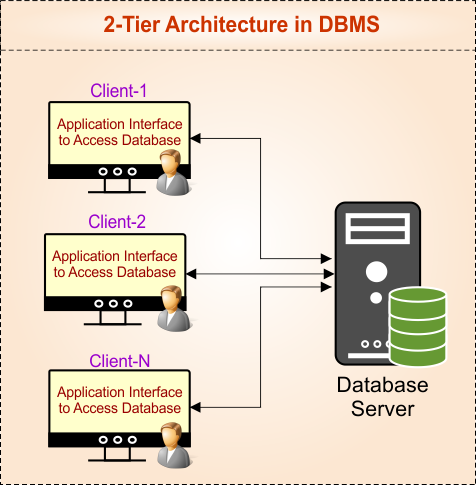
Unlike 1-Tier Architecture, where both the application and database run on the same system, in 2-Tier Architecture, the client and database are on separate machines connected through a network.
- Client Machine: Runs the application software and provides the user interface to send requests.
- Server Machine: Hosts the database, processes queries, and stores all the data.
Features of 2-Tier Architecture in DBMS
- Client-Server Model: The client machine handles queries, forms, reports, etc. It interacts with the server where the database is stored.
- Supports Multiple Users: Numerous clients can connect to the same database simultaneously.
- Requires Network Connection: Clients must connect to the server via a local area network (LAN) or the internet.
- Better Security than 1-Tier: The database is stored on the server, which protects it from being exposed to every user.
- Faster than 3-Tier for Small Systems: The client-server model has less communication overhead compared to multi-tier systems.
- Widely Used in Organizations: It is suitable for departmental and business applications.
Advantages of 2-Tier Architecture in DBMS
Here are some advantages and disadvantages of a 2-Tier Architecture in DBMS are given below
-
Supports multiple users: Many users can access and use the database at the same time.
-
Centralized database management: Database is managed from the server side, making updates and changes easier.
-
More secure than 1-Tier: Users only interact with the application, not the raw database directly.
-
Good performance for small to medium systems: Faster response time compared to 3-Tier for small applications.
-
Data sharing is possible: Different users on different computers can share and update the same information.
-
Scalable for medium projects: Can handle larger databases than 1-Tier systems.
-
Cost-effective: Requires less hardware and infrastructure than 3-Tier, making it cheaper for small organizations.
-
Simple design: Easier to build and manage compared to 3-Tier architecture.
-
Quick communication: A Direct link between client and server makes communication faster.
Disadvantages of 2-Tier Architecture in DBMS
Here are some disadvantages of a 2-Tier Architecture in DBMS
-
Not suitable for very large systems: When too many users connect, the performance becomes slow.
-
High network dependency: If the server or network fails, users cannot access the database.
-
Limited scalability: Cannot grow easily for large enterprises like 3-Tier systems can.
-
Maintenance overhead: Both the client application and the server need updates and compatibility checks.
-
Security risks: Less secure than 3-Tier, because some business logic still runs on the client side.
-
More load on server: Since the server handles both the database and part of the application logic, it may become overloaded.
-
Difficult for large teams: When many developers work on the same system, managing code and updates becomes harder.
-
Less flexibility: Cannot easily separate business logic from database logic, which limits system design.
Examples of 2-Tier Architecture in DBMS
Here are the top 6 examples of 2-Tier Architecture:
i. Online Railway Reservation System
-
Users open the booking application on their computer or mobile.
-
The application connects directly to the central database server that stores train schedules, ticket availability, and passenger details.
-
Users can book, cancel, or check tickets in real time.
ii. Banking Management System
-
Computers in bank branches act as clients.
-
These clients connect to the central banking database server.
-
The server stores account details, transactions, balances, and customer records.
-
When a cashier updates or checks an account, the changes are saved directly in the central server.
iii. Employee Payroll System
-
HR staff use payroll software installed on their computers.
-
The software is linked to a central payroll database server.
-
Employee salary details, attendance, and deductions are stored in the server, and HR can easily update or generate salary slips.
iv. Library Management System (Client-Server Model)
-
Students and staff use library computers (clients) to search for books.
-
All book records, member information, and issued/returned book details are stored in the library’s central server.
-
The system helps in quick searching, issuing, and tracking of books.
v. School/College Student Database
-
Teachers use their computers to enter and check student information.
-
The data (grades, attendance, and personal details) is stored in the school’s central database server.
-
This makes it easy for teachers and administrators to access and update student records anytime.
vi. Hospital Management System
-
Doctors and staff access patient information using client computers.
-
The patient records (medical history, prescriptions, test results, etc.) are stored in the hospital’s central database server.
-
This ensures doctors always have the latest details for better treatment.
Note:
In a 2-Tier, database APIs/drivers (like JDBC, ODBC, ADO.NET, etc.) are used by the client to access the database.
But web APIs (REST/HTTP APIs) are more common in 3-Tier, not 2-Tier.
Conclusion
The 2-Tier Architecture in DBMS follows a client-server model, where clients directly interact with a centralized database server. It provides better data sharing, security, and multi-user support than 1-Tier, making it suitable for small to medium-sized applications like libraries, banks, and schools. However, for large enterprise systems, a 3-Tier architecture is usually preferred due to its scalability and higher security.